Last month, I shared what needs to change — and what must stop — in cybersecurity hiring in 2026.
The feedback was consistent:
“We agree… but execution is where it breaks.”
And that’s the real issue.
Most organisations already know:
• Generic roles don’t work
• Slow hiring creates risk
• Retention is fragile
• The talent market hasn’t got easier
Yet many teams are still stuck in the same cycles.
So what’s missing?
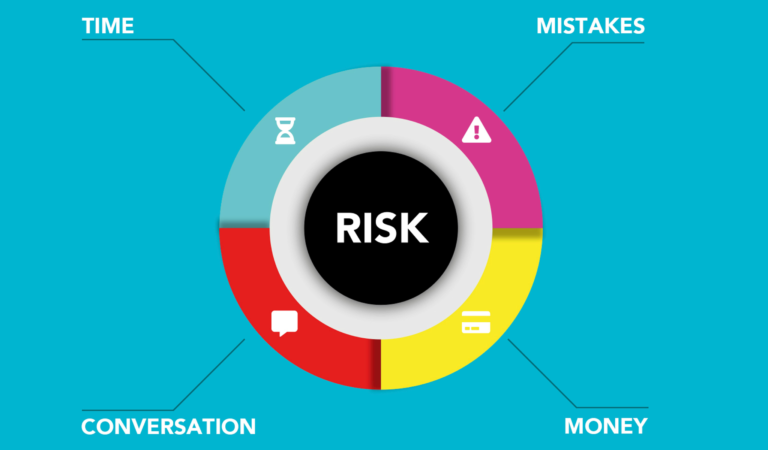
The Execution Gap
Cybersecurity hiring fails in 2026 not because of intent — but because of misalignment.
- Misalignment between risk and roles
Teams hire without first defining the specific threats they’re exposed to. The result? The wrong expertise solving the wrong problems. - Misalignment between speed and quality
Hiring managers are pressured to move fast, but without structure. This leads to rushed decisions, mis-hires, or prolonged vacancies — all of which increase risk. - Misalignment between hiring and retention
Too often, success is measured at offer acceptance, not 6 or 12 months later. That’s where real cost — and security exposure — shows up.
What High-Performing Teams Are Doing Differently
In 2026, the strongest cybersecurity teams are:
- Treating hiring as a risk-reduction strategy, not a resourcing task
- Defining roles based on actual operational challenges
- Streamlining decision-making without compromising rigour
- Building retention into the hiring process — from day one
They’re not hiring more.
They’re hiring smarter.
The February Question
As we move deeper into 2026, here’s the question worth asking:
Does your cybersecurity hiring process reduce risk — or quietly create it?
Because in this market, standing still is not neutral.
Curious to hear from CISOs, CTOs, and security leaders:
What’s the biggest blocker you’re seeing right now — speed, clarity, or retention?