Cybersecurity Hiring Myths—What’s the Biggest One You’ve Heard?

The cybersecurity talent gap is real—but are we making it worse by holding onto myths that limit hiring? Too often,…
Interesting article from Chainalysis.com on the decline in ransomware payments

Key factors: 1. A reluctance to pay 2. Heightened law enforcement efforts 3. The takedown of one of the most…
The Cybersecurity Sales Professional profile type is — Persuader
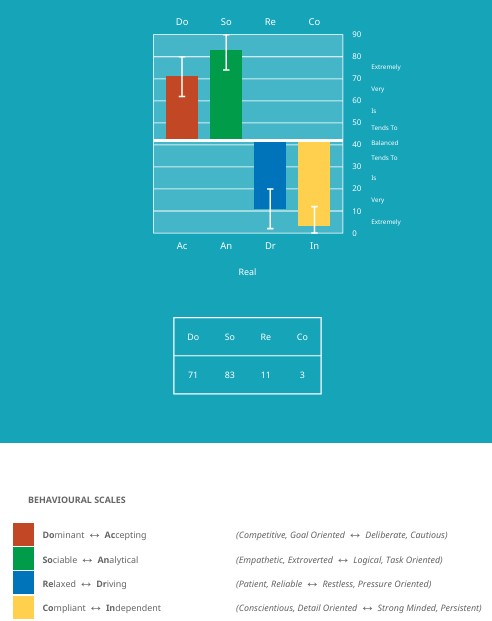
As part of our main focus to align cybersecurity challenges with the right expertise. We use the triple lock formula…
The Hidden Talent Pools That Companies Overlook in Cybersecurity Hiring

The cybersecurity talent shortage is real, but what if the right talent is hiding in plain sight? Many companies struggle…
The Most In-Demand Cybersecurity Skills for 2025

The cybersecurity talent gap isn’t closing anytime soon—so what skills will be in the highest demand next year? Based on…
The InfoSec Risk Analyst profile type is — Specialist.
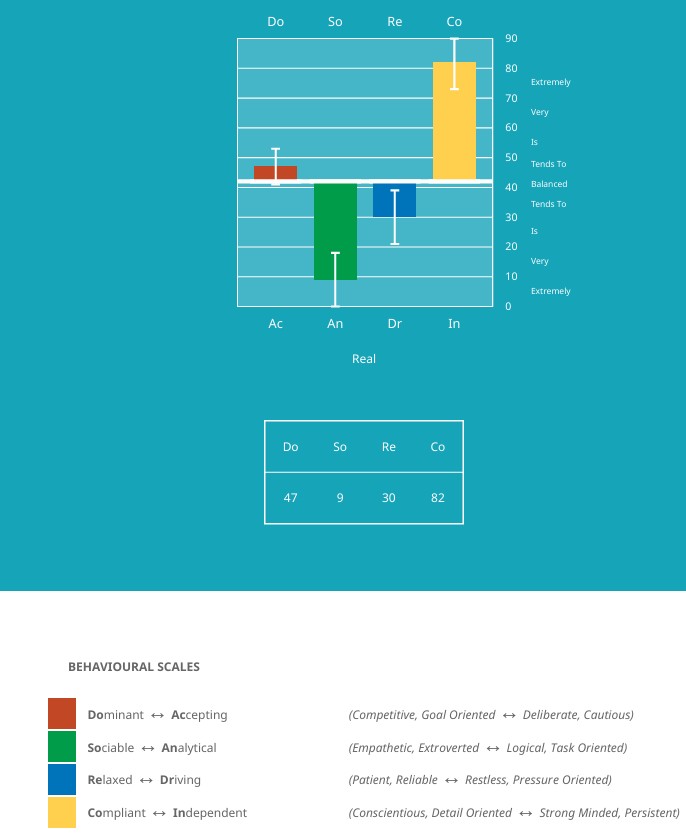
As part of our main focus to align cybersecurity challenges with the right expertise. We use the triple lock formula…
Supply Chain Attacks: the silent threat in the ecosystem

In today’s interconnected world, no organization operates in isolation. While this interconnectedness fuels innovation and efficiency, it also opens the…
Defending Smart Cities Infrastructure in a Digital World

As cities become smarter, integrating IoT devices, AI-powered systems, and connected infrastructure to improve quality of life, they also become…
The Security Architect profile type is — Transition
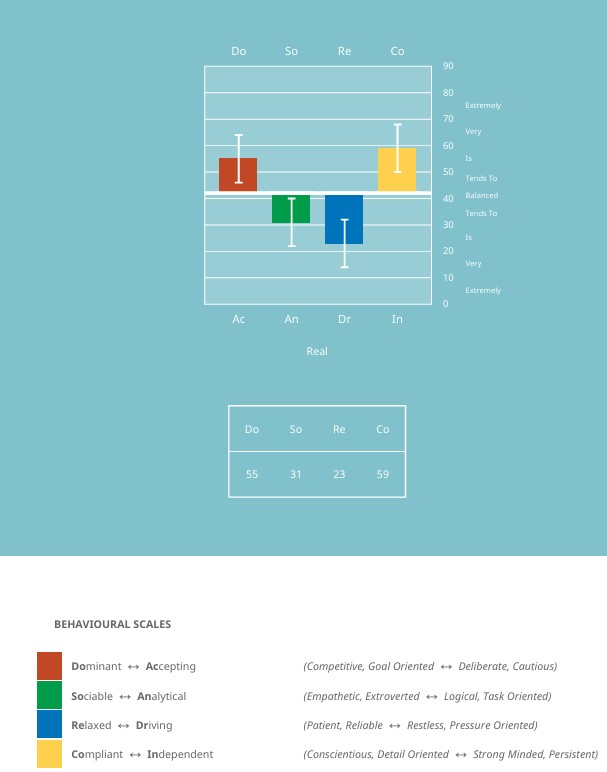
As part of our main focus to align cybersecurity challenges with the right expertise. We use the triple lock formula…
Insider Threats in OT/ICS: Overview, Challenges, and Solutions

Insider threats in Operational Technology (OT) and Industrial Control Systems (ICS) are an evolving concern in cybersecurity. These environments control…
